Stay Ahead of Evolving Data Threats–Identify Gaps, Protect Your Assets, & Stay Secure
Your business faces relentless cyber threats to sensitive data, risking costly breaches, compliance failures, and reputational damage. Cyphlon’s data security posture management empowers you to take control—proactively identifying vulnerabilities, enhancing compliance, and fortifying your data against emerging threats.
Minimize the risk of data breaches by identifying vulnerabilities before they can be exploited, ensuring stronger data protection.
Stay effortlessly compliant with industry standards like HIPAA, GDPR, and SOC 2, reducing regulatory risks and penalties.
Prevent costly disruptions with a proactive data security approach that safeguards operations and helps achieve consistent service availability.
Reduce long-term costs associated with data breaches, non-compliance, and data recovery through proactive risk management.
Cyphlon’s cybersecurity specialists bring years of hands-on experience, helping businesses across industries secure their data with proven strategies and frameworks.
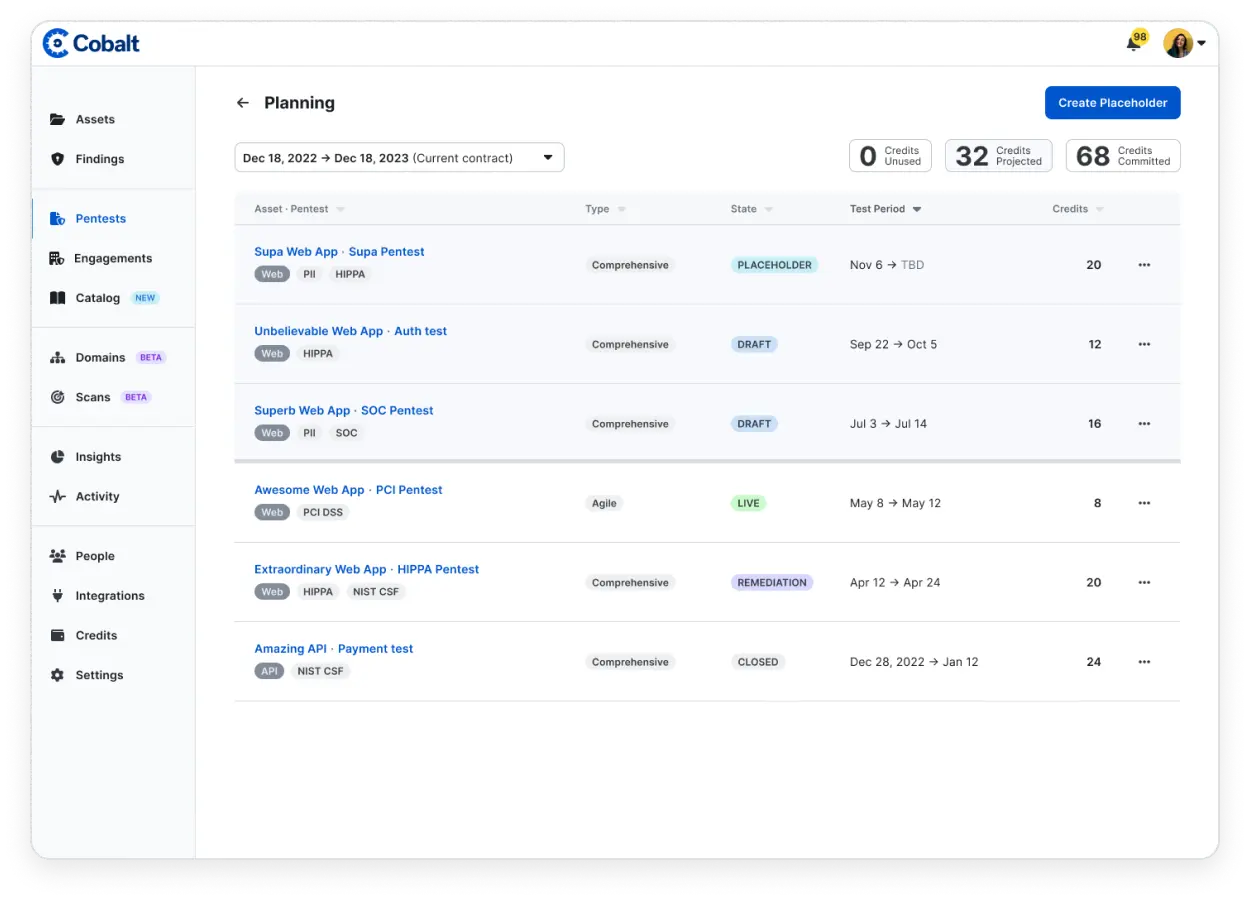
We customize our data security strategies to match your industry standards, compliance requirements, and unique risk landscape—delivering targeted protection.
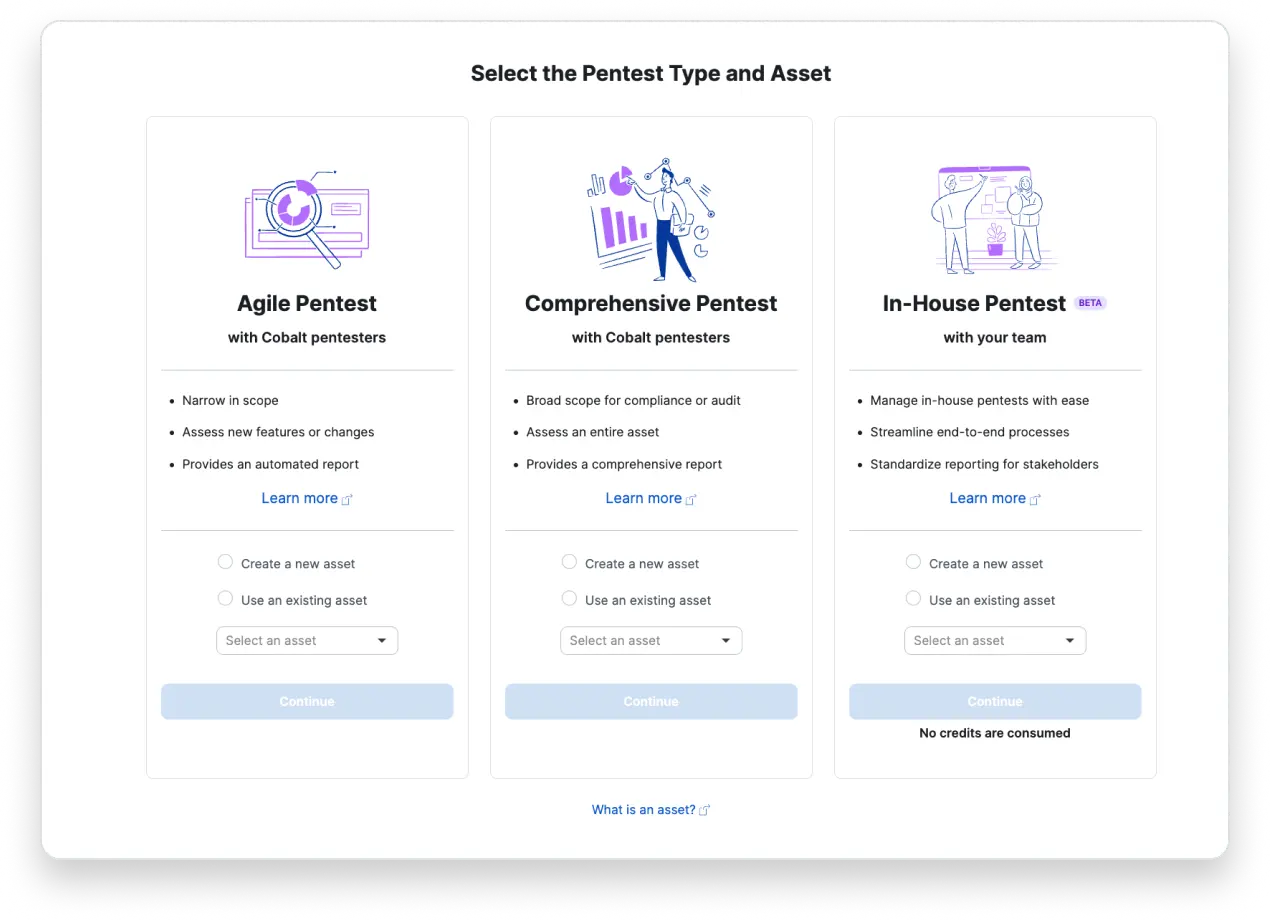
Our experts leverage cutting-edge technologies and frameworks to identify and mitigate risks, safeguarding your data against evolving threats.

Receive executive-friendly reports with prioritized recommendations, empowering informed decision-making without overwhelming technical jargon.

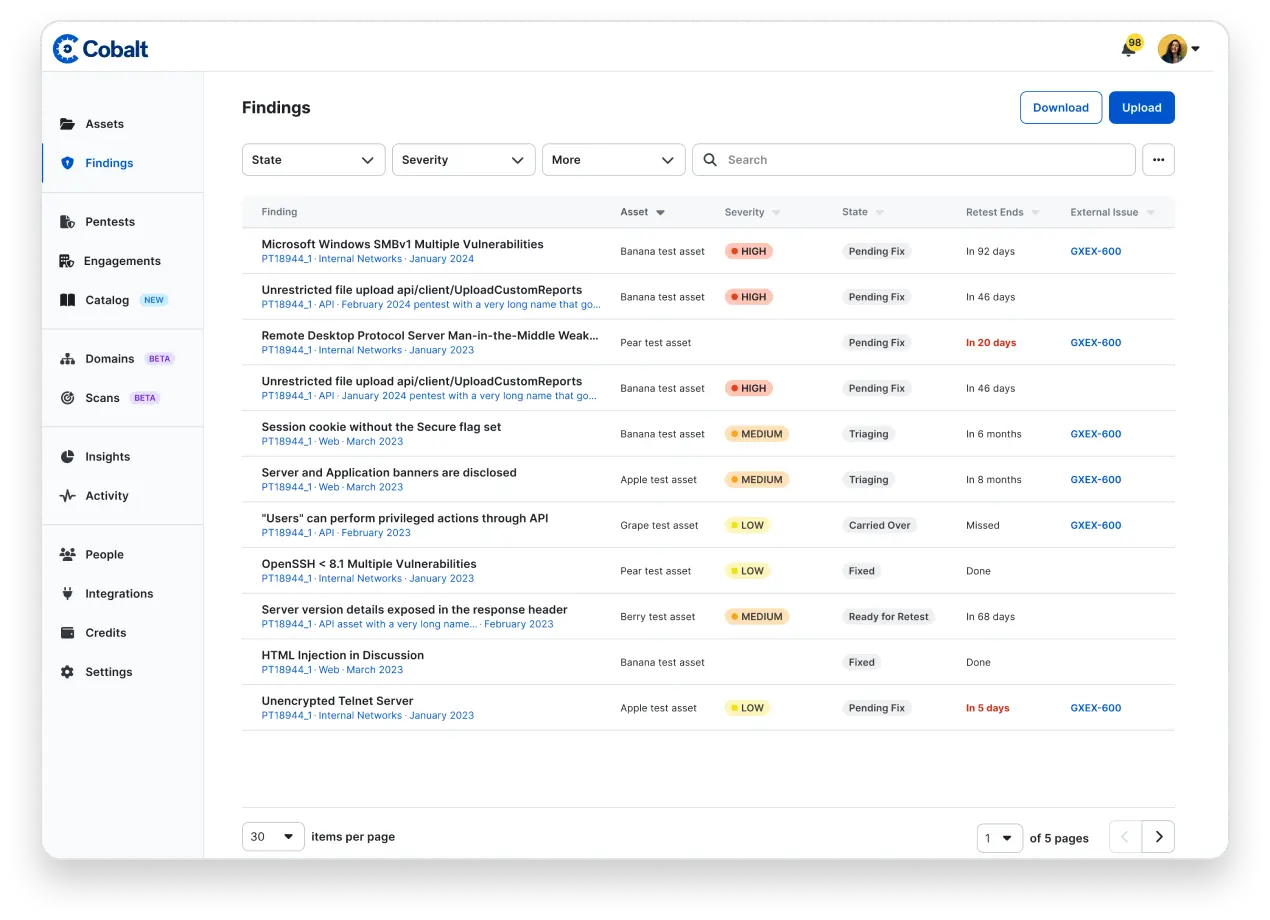
Cyphlon’s cybersecurity specialists bring years of hands-on experience, helping businesses across industries secure their data with proven strategies and frameworks.
We customize our data security strategies to match your industry standards, compliance requirements, and unique risk landscape—delivering targeted protection.
Our experts leverage cutting-edge technologies and frameworks to identify and mitigate risks, safeguarding your data against evolving threats.
Receive executive-friendly reports with prioritized recommendations, empowering informed decision-making without overwhelming technical jargon.
Gain clarity, control, and confidence with a comprehensive data security approach for lasting protection.
At Cyphlon, we use advanced tools, tailored strategies, and industry expertise to safeguard your business from data breaches and compliance risks.
Ready to fortify your data security posture?
